Drive-by Attacks
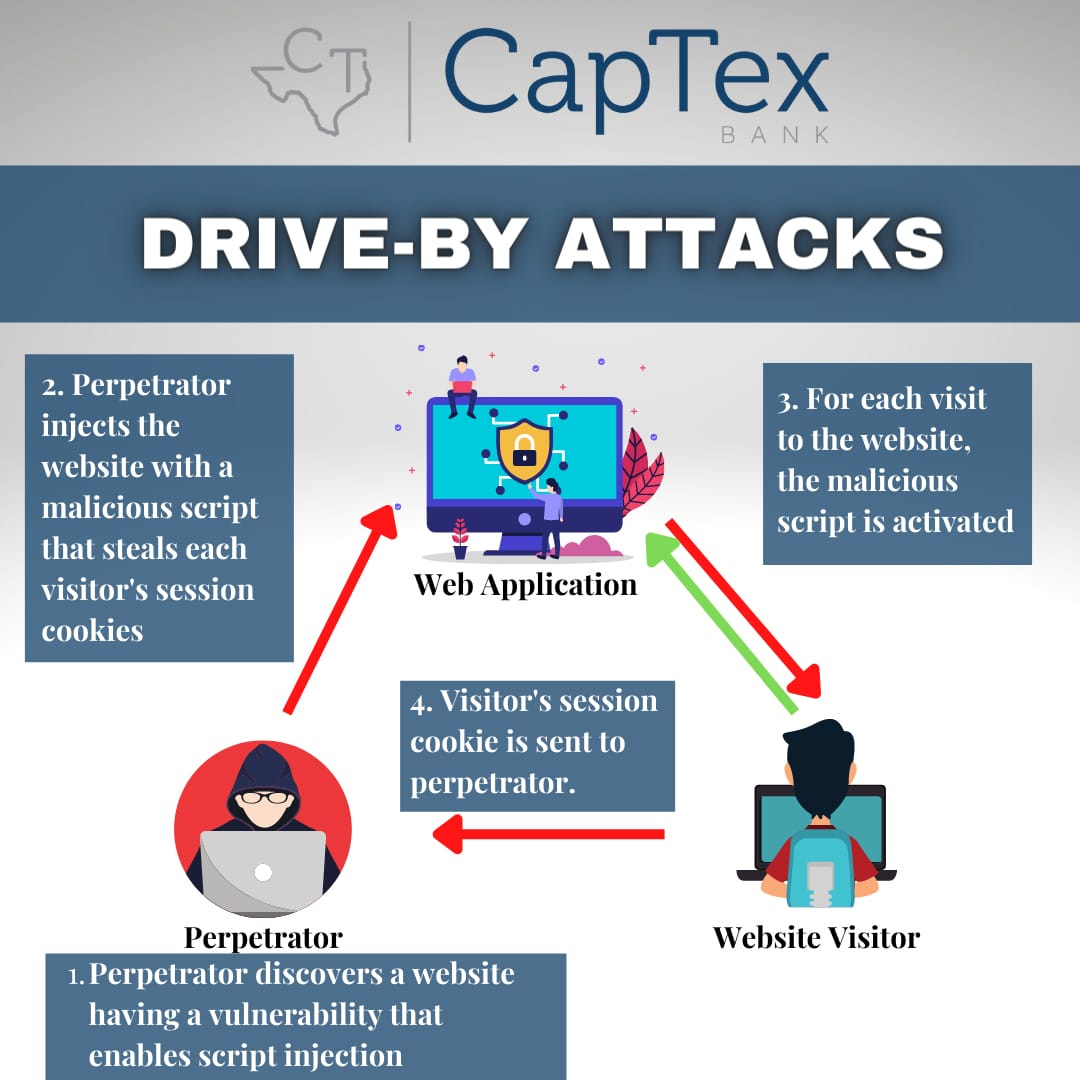
Drive-by attacks or drive-by downloads are the infection of a computer with malware when a user visits a malicious website. Drive-by attacks occur without the knowledge of the user. Simply visiting an infected website may be sufficient for the malware to be downloaded and run on a computer.
Malware exploits vulnerabilities in a user’s browser (and browser plugins) in order to infect their computer. Exploits take advantage of a weakness in order to access or infect the computer. Usually an exploit takes advantage of a specific vulnerability in an application and becomes obsolete when that weakness is patched.
Hackers continually attack legitimate websites in order to compromise them, injecting malicious code into their pages. Then, when a user browses that legitimate (but compromised) site, the injected code is loaded by his/her browser, which initiates the drive-by attack. In this manner, the hacker can infect users without having to trick them into browsing a specific site.
Drive-by downloads represent a different distribution technique, attack intensity, and level of sophistication from threat actors. These attacks often go unrealized but can cause significant harm.
Here are a few examples of the consequences of a drive-by attack:
- Downloaded malware may go undetected on a computer or other device for a long period of time. This is the reason that these types of threats are able to collect any type of data within the device and store the information remotely.
- On the flip side, some malware may immediately take control of a device, locking down the entire system and often destroying the device.
- Botnets represent a significant portion of many drive-by attacks and this type of malware targets devices with vulnerable endpoints across the internet, rather than targeting specific individuals, companies or industries. As more and more devices are brought into a botnet scheme through drive-by infiltration, the more powerful the threat becomes, allowing it to further corrupt networks.
Where typically, an individual will need to click on a link, press a key to download, or open a malicious email, a drive-by download passes on small pieces of code from a compromised website and all an innocent website visitor has to do is visit a site and the code can be downloaded. These are considered dangerous types of cyber-attacks because they do not require any action on the part of the unsuspecting victim.
To defend against drive-by downloads, you should have endpoint security software coupled with web security filtering. To defend against exploits to your computer’s operating system or applications, you should make sure your antivirus or endpoint security software is active and your computers are fully patched. Avoid becoming infected by not using administrator user account access to browse the internet or read emails. Utilize system firewalls and install operating system and application security patches. Lastly, ensure you are using a robust anti-malware/anti-virus endpoint protection application and make certain that it, too, is receiving regular updates and is performing routing scans (if not real-time scans) on your devices.

