Zero-Day Attacks
The term “zero-day” refers to the fact that a software or system vendor or developer has only just recently discovered a security vulnerability flaw that hackers could use to attack. A zero-day exploit takes place when cybercriminals exploit the flaw before the developers have the chance to correct the flaw.
Stated in more detail, a zero-day vulnerability is a software vulnerability discovered by attackers before the vendor has become aware of it and since they are unaware, no security software patch exists for the vulnerability, making attacks likely to succeed.
A zero-day exploit is the method hackers use to attack systems with a previously unidentified vulnerability. And a zero-day attack is the use of a zero-day exploit to cause damage to or steal data from a system affected by a vulnerability.
Hackers will use vulnerable software to create havoc, often spotting a vulnerability before the software developers can remediate. While the vulnerability is still open, attackers can write and implement a code to take advantage of it and this is known as exploit code. The exploit code may lead to the software users being victimized – for example, through identity theft or other forms of cybercrime. Once attackers identify a zero-day vulnerability, they need a way of reaching the vulnerable system.
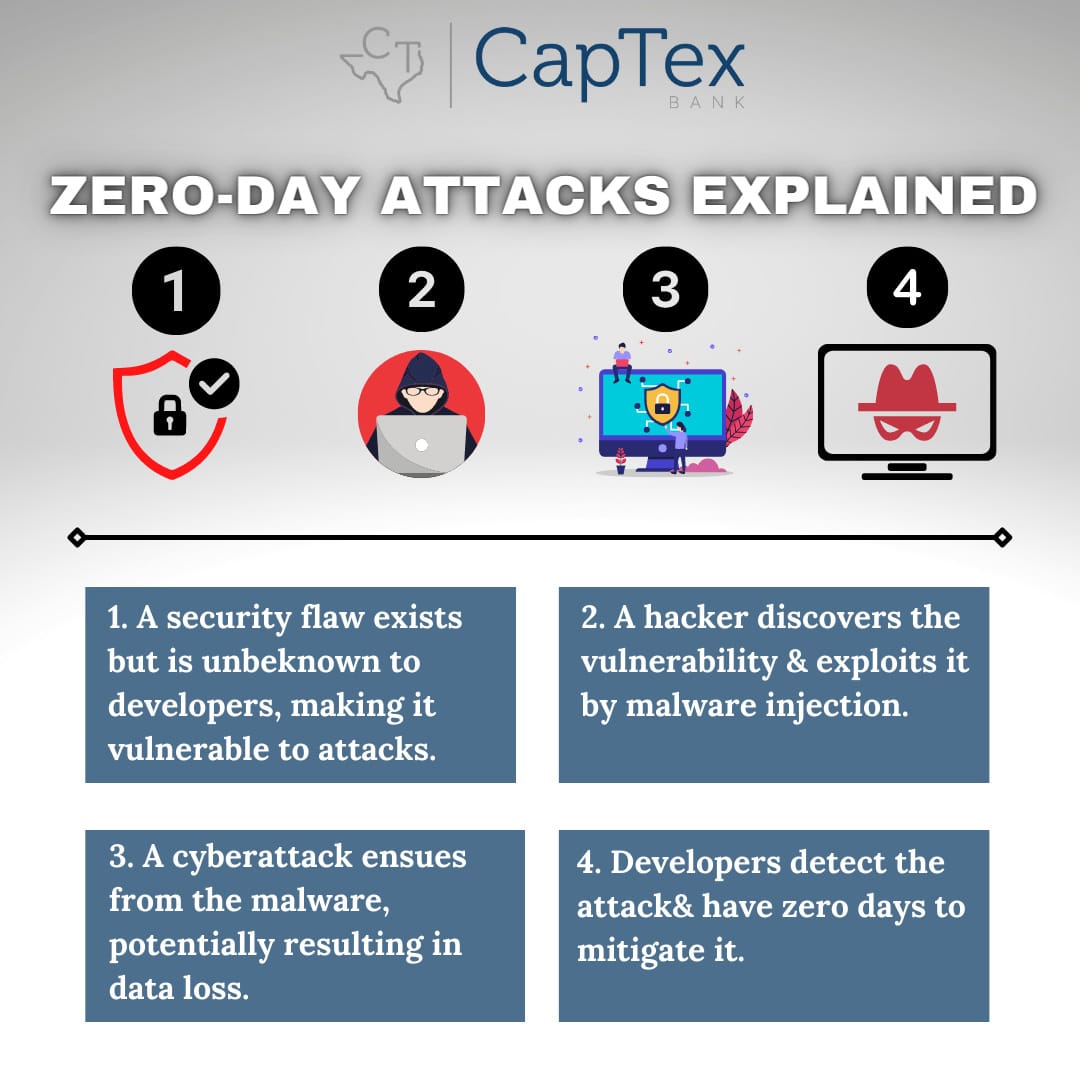
They often do this through a socially engineered email. This email appears to be from a known or trusted correspondent but it is actually being sent by an attacker. The message will try to convince a user to perform an action like opening a file or visiting a malicious website. Doing so would then download malware, invading the user’s files and stealing confidential data. Exploits such as this may also be sold on the dark web for large sums of money, making these attacks especially dangerous because the only people who know about them are the cyber criminals themselves.
Because zero-day vulnerabilities can take multiple forms – such as missing data encryption, missing authorizations, broken algorithms, bugs, and problems with password security – they can be challenging to detect. Due to the nature of these types of vulnerabilities, detailed information about zero-day exploits is available generally after the exploit is identified. For zero-day protection and keeping your computer and data safe, it is essential to follow cyber security best practices:
- Keep all software and operating systems updated by applying security patches.
- Use only essential applications, reducing the risk to your network.
- Use a firewall and configure it to allow only necessary traffic and/or transactions.
- Within business or organizations, educate users to use good safety and security habits when online.
- Use a comprehensive anti-virus software security solution that blocks known and unknown threats.

