Distributed Denial of Service Attacks
Distributed Denial of Service (DDoS) attacks are a popular cyber threat that utilizes sophisticated techniques to attack network systems. They are a malicious attempt to disrupt services where normal network traffic becomes overwhelmed with a coordinated “flood” of traffic; therefore, denying any legitimate access to the service. This type of attack becomes possible by bridging various types of computers and devices into a centrally controlled botnet and collectively pointing them towards a target endpoint. To emphasize, multiple systems are required to carry out a DDoS attack successfully.
There a variety of ways in which to disrupt a network’s resources and hackers have found a variety of ways in which to disrupt services. Using botnets and automation for issuing requests demand the targeted devices to employ more computational power to handle them and frequently they are successful. DDoS attacks are divided into three types:
- The first type involves a hacker saturating network bandwidth and include flooding network traffic.
- The second type of attack is initiated by targeting vulnerabilities in the network, intending to consume computational resources and impacts infrastructure, such as firewalls. Flaws in network design may allow attackers to overload a server with communication requests.
- The last type of attack includes flooding requests for images, files or other file size assets and are intended to crash a server.
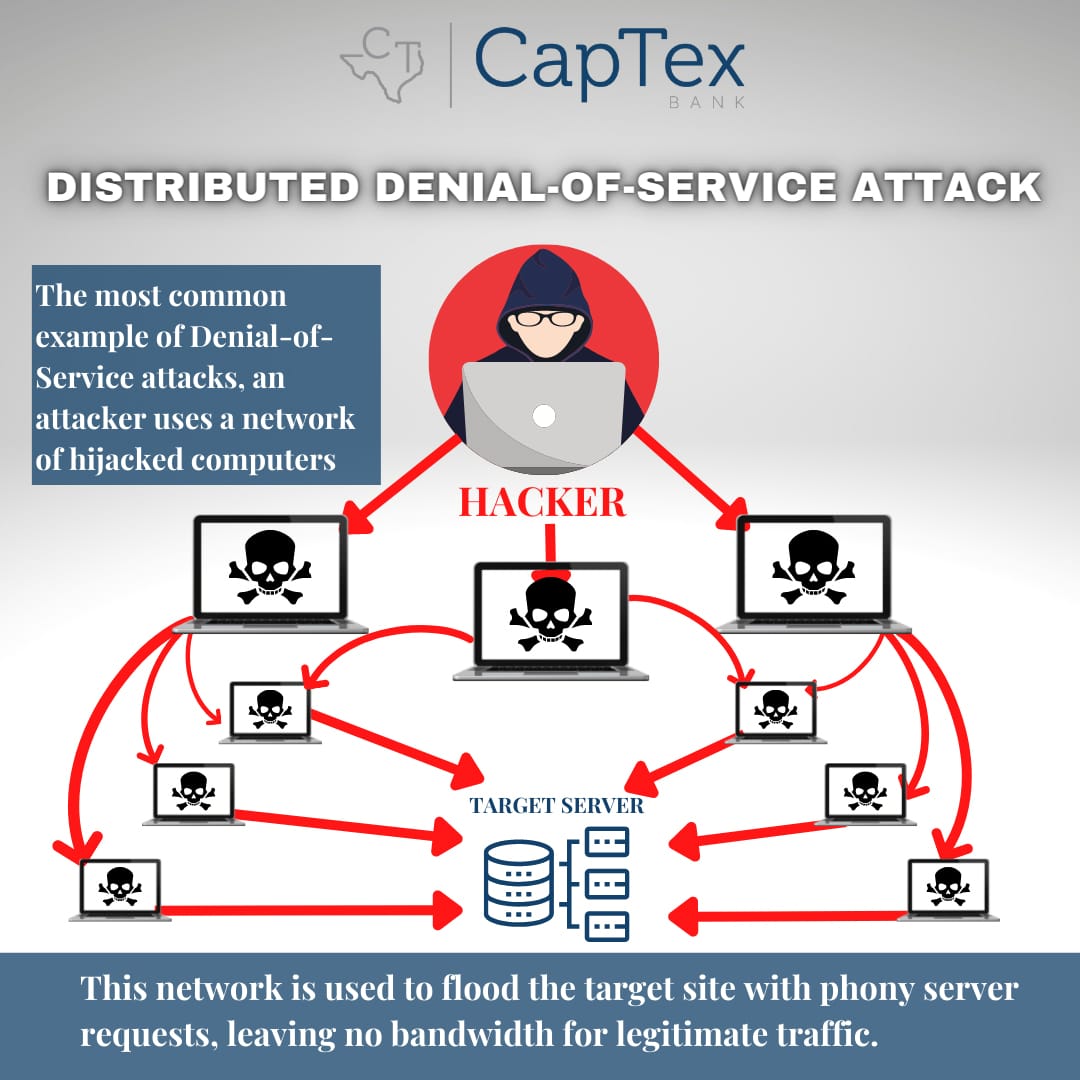
DDoS attacks create more requests to a server than it can handle, thus refusing the incoming requests of legitimate network traffic and customer requests. As websites are the common gateway to business services, disrupting a web server’s capacity to handle requests can temporarily take a company offline. These types of service disruptions and outages have the potential to cause a significant financial loss resulting in irreparable reputational damage. This affects customer trust and satisfaction and this is why DDoS prevention techniques are significant.
Detecting DDoS attacks depend on the attack size, the targeted server’s sufficiency to handle the incoming requests, and whether or not any uptime or performance monitoring systems are already deployed to trigger alerts. The immediate impact of attacks can range from intermittent performance issues such as slow form submissions and page rendering, to issuing webpage error messages or complete server crashes. Prevention measures may include:
- On-Premise Firewalls
- Integrated Network and Cloud Security solutions
- Network Traffic and Application monitoring solutions
- System Security Event Logging
- Real-time Capacity Management and Load Balancing products
- Machine Learning solutions
A few of the top industries that face these types of attacks include gaming, software information services, film, finance, e-commerce and advertising and media information. DDoS attacks trend during the holiday season, while consumers are conducting online transactions. Drops in cryptocurrency value also plays a part in the intensity of DDoS attacks since botnet owners tend to deploy when cryptocurrency prices fall. Regardless of who is deceived or when the attacks occur, DDoS attacks are increasing and the best prevention is being prepared. Continually identifying areas of weakness/vulnerabilities and making sure DDoS protections work before an attack occurs is the best way to prevent detrimental downtime.


