Cross-Site Scripting
Cross-site scripting (also known as XSS) is a web security vulnerability that allows an attacker to compromise the interactions that users have with a vulnerable application.
It is one of the most common methods hackers use to attack websites. It allows an attacker to execute JavaScript when other users visit your website, which is designated to segregate different websites from one another.
Cross-site scripting vulnerabilities normally allow an attacker to masquerade as a victim user, to carry out any actions that the user is able to perform, and to access any of the user’s data. If the victim user has privileged access within an application, then the attacker might be able to gain full control over all of the application’s functionality and data.
Cross-site scripting works by manipulating a vulnerable web site so that it returns malicious JavaScript to users. When the malicious code executes inside a victim’s browser, the attacker can fully compromise their interaction with the application.
There are three main types of XSS attacks:
- Reflected XSS – malicious script is received from a website visit and executed within the browser
- Stored XSS – malicious script is received from a website’s database
- DOM-based XSS – vulnerability exists in client-side code rather than server-side code
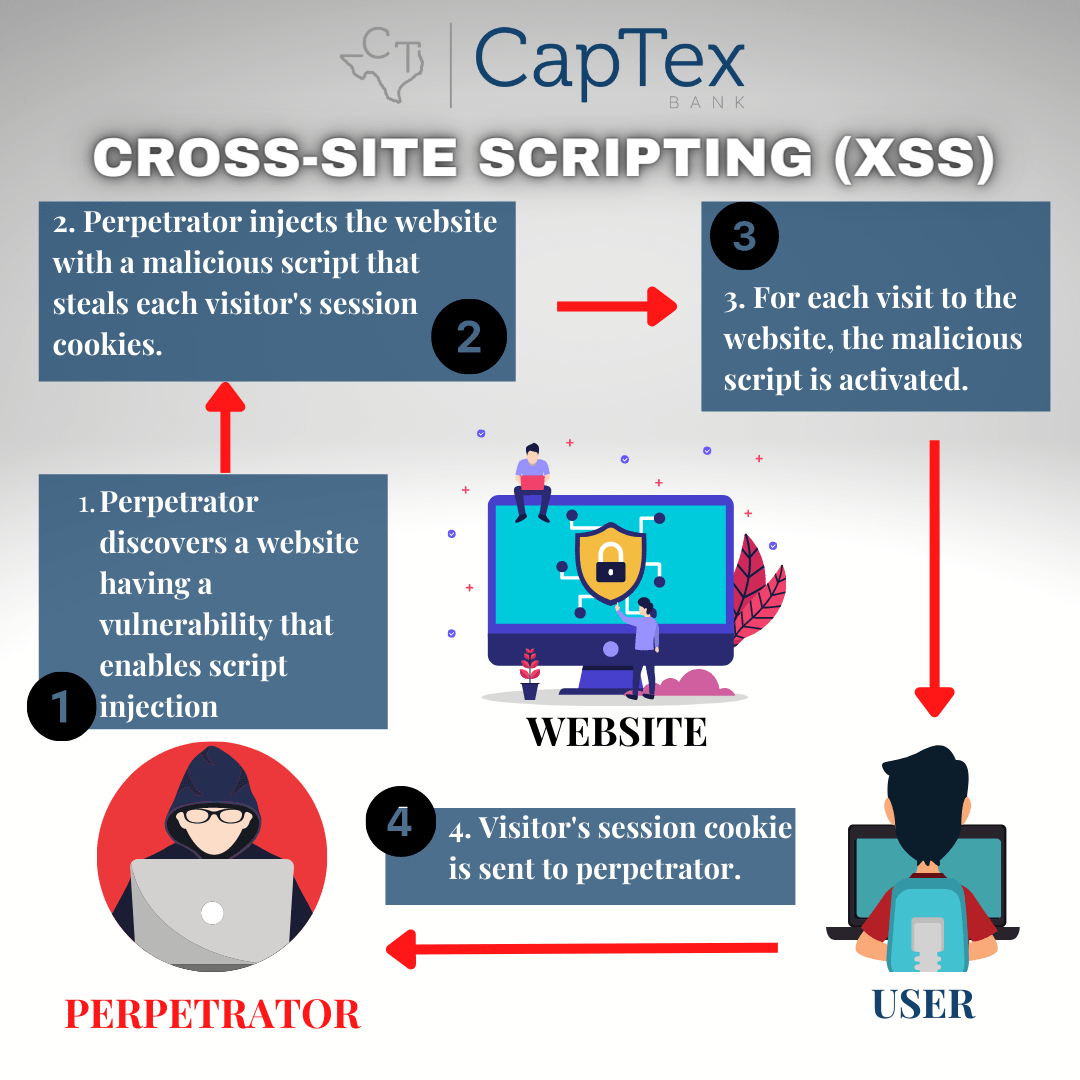
An attacker who exploits a cross-site scripting vulnerability is typically able to:
- Impersonate or masquerade as the victim user
- Carry out any action that the user is able to perform
- Read any data that the user is able to access
- Capture the user’s login credentials
- Perform virtual defacement of the web site or leave it unusable
- Inject trojan functionality into the web site
- Spread malware on social media sites
- Steal a victim’s identity (Identity Theft) or sensitive data
- Commit financial fraud within banking websites
The actual impact of an XSS attack generally depends on the nature of the application, its functionality and data, and the status of the compromised user. For example, in an application holding sensitive data, such as banking transactions, emails or healthcare records, the impact will be significant.
Preventing cross-site scripting is trivial in some cases but can be much harder depending on the complexity of the application and the ways it handles user-controllable data. In general, prevention normally involves a combination of the following measures:
- Web Application Firewall – Appliance that looks for known attack methods and blocks them
- Content Security Policies – An allowlist that prevents content from being loaded by restricting what an attacker can perform
- Cookie Attributes – Limit the impact of an XSS attack
- Patch Software – Keep software up-to-date in order to fix bugs, improve performance, install new features and address security vulnerabilities
While cross-site scripting is a website vulnerability that was born in the 1990’s, XSS is still very prominent today.

