Eavesdropping Attack
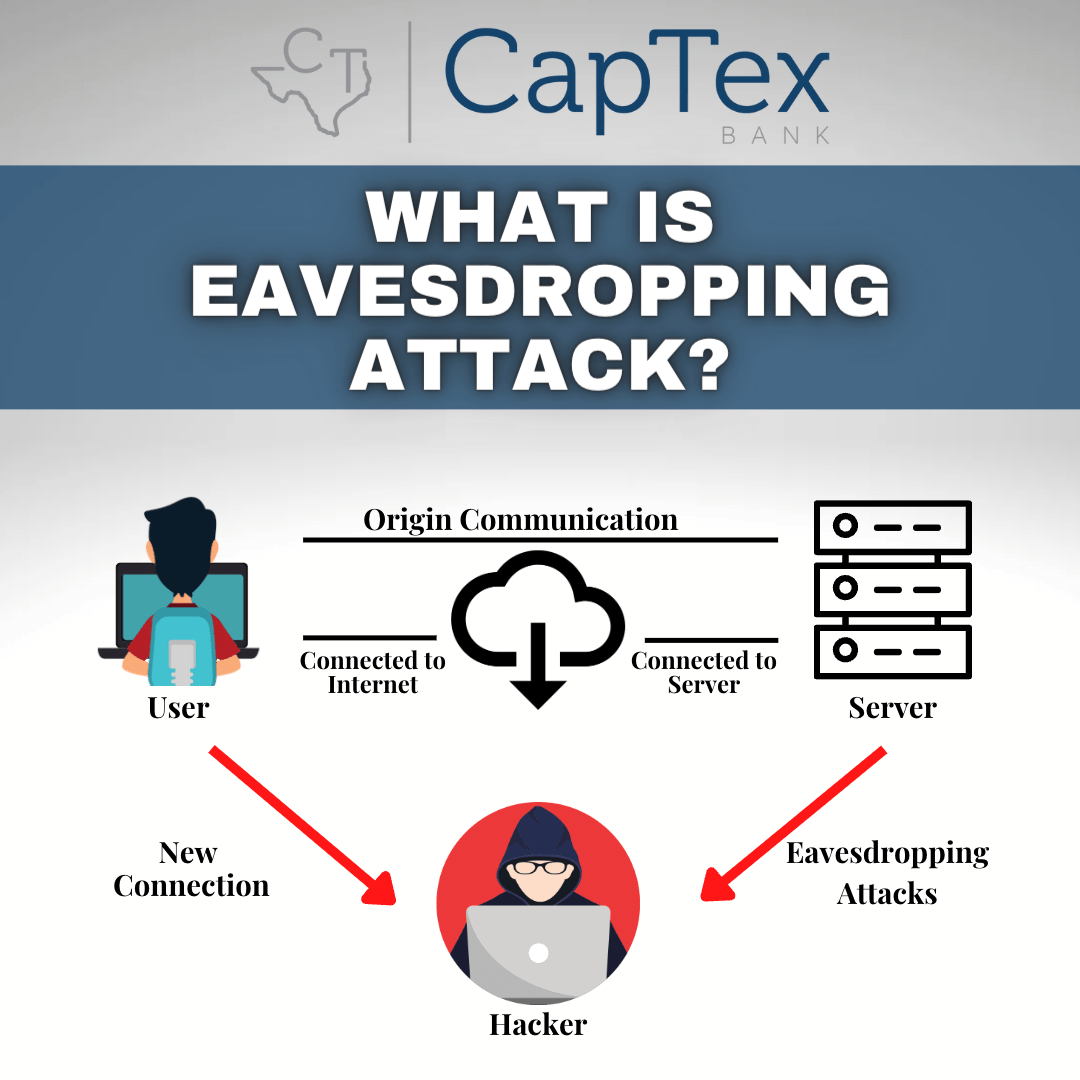
An Eavesdropping Attack is conducted when a computer, smartphone, tablet, wearables, or other connected device steals information while it is transferred on a network. The attack uses network communications that is unsecured to get access to data when it is sent or received by the user.
The attacker looks for important financial and corporate data that can be monetized for illicit purposes. Because network transmissions appear normal, eavesdropping attacks can be difficult to detect.
An eavesdropping cyber attack involves a weaker network connection between a client and a server that can be used by the attacker to reroute network traffic to be successful. On a computer or a server, the attacker downloads and installs special network monitoring software with the name “sniffer” that will seek out and report (intercept) sensitive data communications as they are being transferred.
The recorded and captured data packets are then analyzed using advanced cryptographic tools, or they simply read the obtained data or conversation, in order to capture valuable information. Any device in the network between the sending and receiving devices, as well as the initial and terminal devices themselves, is a point of weakness.
Eavesdropping cyber-criminals are always listening and can be located anywhere trying to obtain sensitive personal information from vulnerable or unsecure websites. These cyber-criminals are trying to view bank account information, spending or purchases, social media posts, applications or registrations and appointments. Connected devices often contain contacts, photos, videos, location, health and financial data – all which is data that can be used against an innocent victim for the purpose of making unauthorized purchases, transferring money to their own accounts, stealing your identity to impersonate you, which may include committing crimes in which to blame an innocent victim, using incriminating evidence gathered in order to blackmail or extort victims, using stolen passwords to gain access to private or corporate networks, and selling a victims information in order to make a quick and easy profit.
In order to defend against an eavesdropping attack, a firewall must be in place other than relying on the default operating system firewall. Real-time anti-virus/anti-malware must be installed and updated at all times. A Virtual Private Network (VPN) service should be used to hide your identity on the Internet. Strong passwords must be in use, as well as changed periodically and not repeated across other online accounts. Avoid using public Wi-Fi networks, such as those offered for free in coffee shops and airports, for critical online applications and/or transactions. Avoid clicking on suspicious website links as doing so may result in infecting your computer with malware. Mobile apps should only be downloaded from the official Android or Apple store. Virtual assistants such as Amazon’s Alexa or Google Home, and their “always-on” state makes security monitoring a challenge as well.


