Malware
Malware is one of the greatest cyber-security threats encountered today, continuing to increase year over year, with ransomware in the lead.
Networks must be monitored to catch and contain malware before it can cause extensive system damage. Prevention is key and in order to prevent an attack, it is critical to understand the nature and common types of malware.
Malware (or malicious software) is used by threat actors to intentionally infect devices. There are many categories that fall within the term “malware”:
- Viruses – Requires human intervention and is malicious code that spreads throughout systems, infecting devices and replicating itself.
- Worms – Does not require human intervention and inserts itself within devices via security vulnerabilities or malicious files or links. Worms often go unnoticed and may be disguised as legitimate work files.
- Ransomware – Encrypts files or devices and forces victims to pay a ransom in exchange for re- entry.
- Bots – Self-replicating malware that spreads to other devices, creating a network of bots or a botnet. Botnets are commanded by the attacker to perform automated tasks and are often used in DDoS (Distributed Denial of Service) attacks. They can also conduct keylogging and send phishing emails.
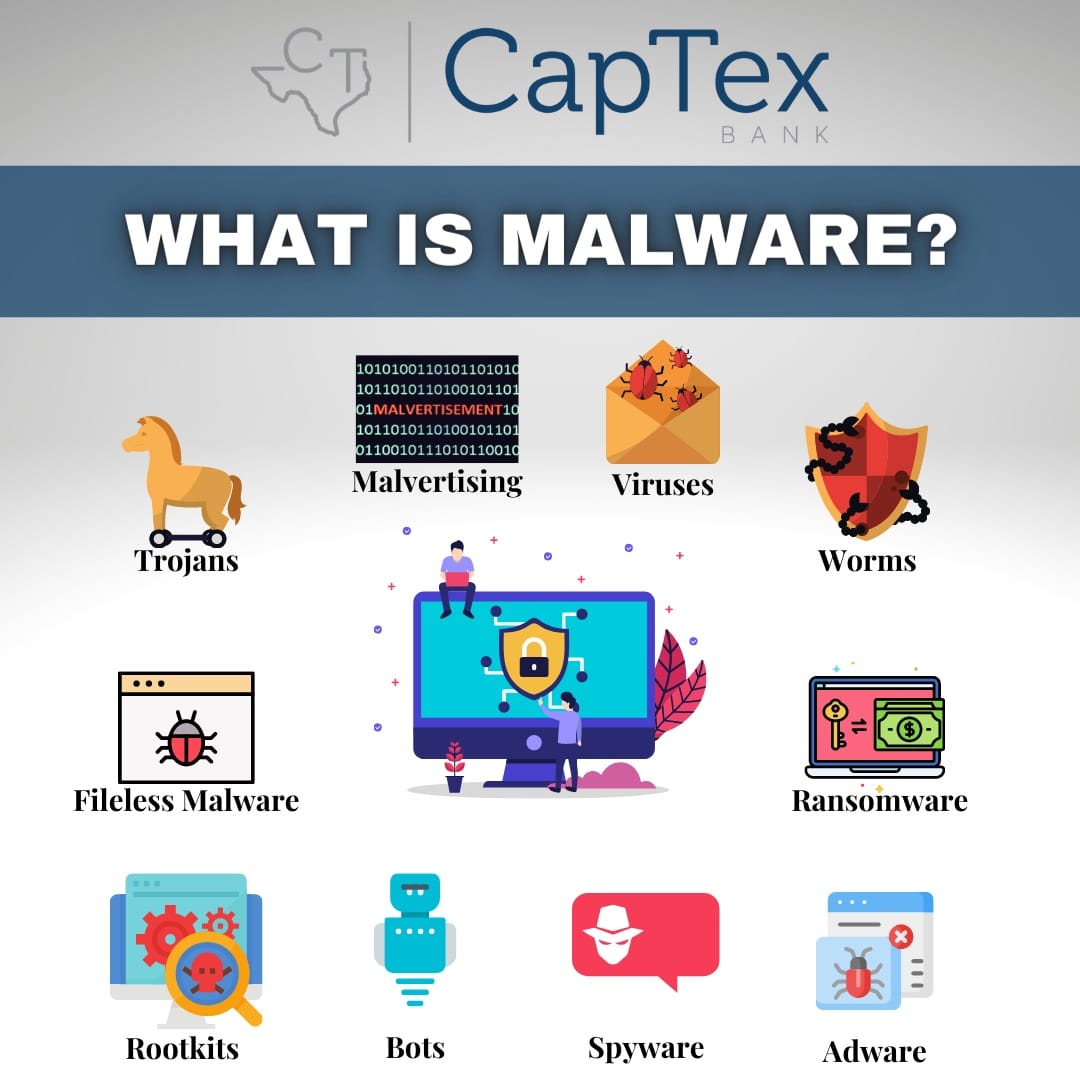
- Trojan horses – Malicious software that appears legitimate to users and rely on social engineering techniques to invade devices. Once within a device, the Trojan’s malicious code is installed and backdoor system access to a device is granted.
- Keyloggers – Surveillance malware that monitors keystroke patterns to obtain victim’s usernames and passwords and other sensitive data. Keyloggers can be either hardware or software – either a keyboard is used or malicious software is downloaded by the victim.
- Rootkits – Malicious software that enables threat actors to remotely access and control a device. They can deactivate endpoint anti-malware and anti-virus software.
- Spyware – Malware that downloads onto a device without the user’s permission, stealing user’s data to sell to advertisers and external users. It can steal user credentials and obtain bank details and other sensitive data. It infects devices through malicious apps, links, websites and email attachments.
- Cryptomining malware – Threat actors use an infected device’s resources to conduct the process of verifying transactions within a blockchain.
- Adware – Software that displays or downloads unwanted advertisements, typically in the form of banners or pop-ups and collects web browser history and cookies to target users with specific advertisements.
Malware invades physical systems, from suspicious email or via the internet. Phishing, which involves email that appears legitimate but contains malicious links or attachments, is one of the most common malware attack points. Other entry point methods used are infected USB drives, unpatched or fraudulent software and applications, insider threats, and vulnerable or misconfigured devices and software.
Malware can go undetected for extended periods of time. Many users are only aware of a malware attack if they receive an anti-malware alert, see pop-up ads, are redirected to malicious websites, or experience slow computer performance. Attackers use malware to steal data and user credentials to spy, hold devices hostage, damage files and much more.
The best defense against the common types of malware attacks is strong cybersecurity:
- Patch and update software
- Use firewalls and security software (anti-malware)
- Follow email best practices
- Deploy email security gateways
- Avoid suspicious links and attachments
- Implement access control
- Require multifactor authentication
- Use the principle of lease privilege
- Monitor for abnormal or suspicious activity
- Perform regular security awareness training to teach users the dangers of the different types of malware and to urge caution when clicking on links and downloading files

