Man in the Middle
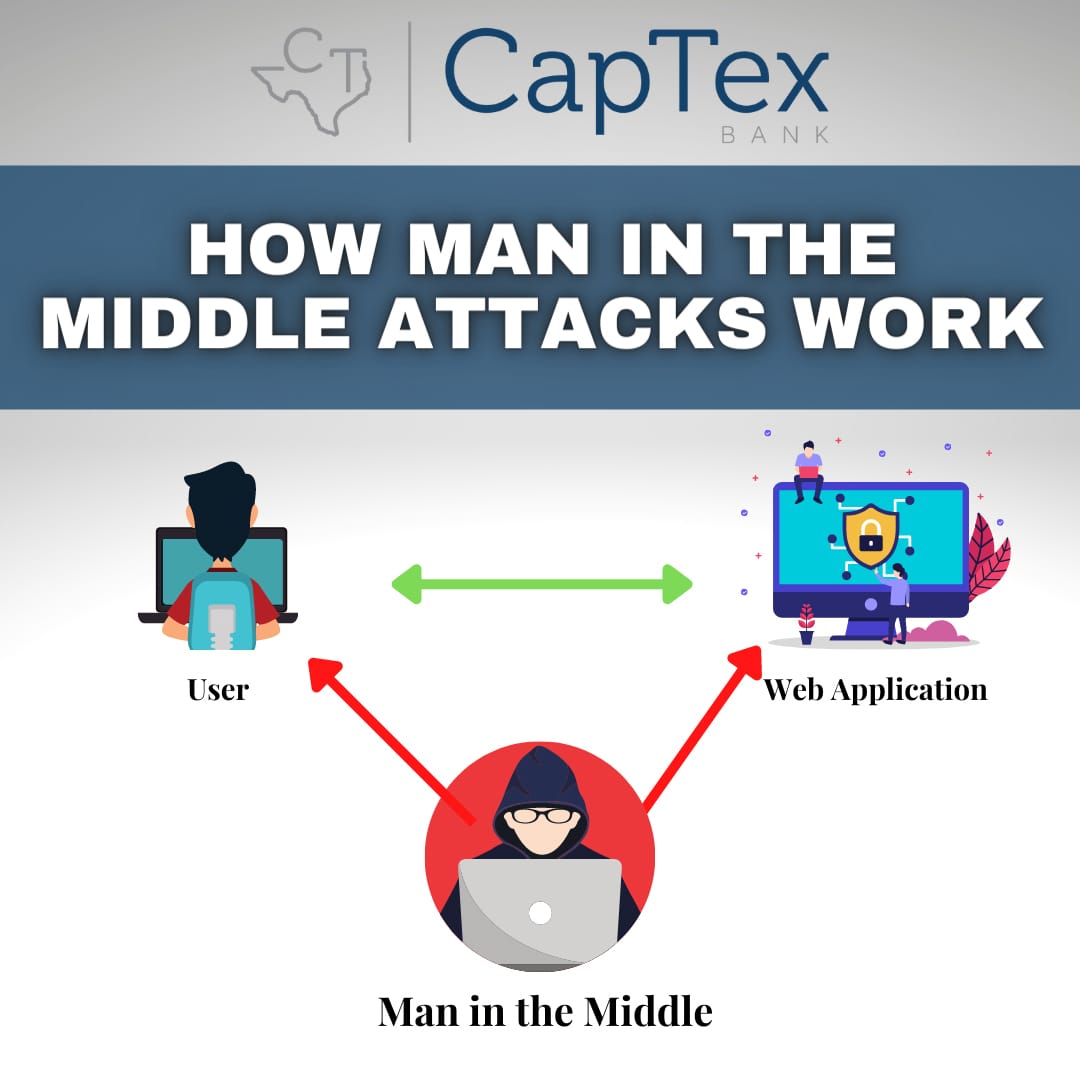
A Man in the Middle attack (or MITM in short) is a type of cyberattack where the attacker puts themselves between a person and an application or website. It is a very popular hacking tactic where the victim’s communications are intercepted by the hacker. The attacker then eavesdrops on the conversation between the two.
If a hacker manages to successfully carry out an unauthorized MITM attack, there are many types of damage that can be done, for example, stealing your personal information, account credentials, bank account details, users and passwords or installing a backdoor to your device.
These attacks may involve accessing and damaging business computer systems, online stores or data backup or file storage.
There are several hack types that fall under the MITM umbrella:
- DNS Spoofing: The most common type of MITM attack. An unsuspecting victim connects to a secure website, such as personal online banking. The hacker intercepts the connection and redirects the victim to a fake website that looks and feels exactly like the legitimate website. The only difference is that the hacker has a clear view of everything in real-time, including what username/password is being typed into the website. The fake website may also be used to install types of malware onto the victim’s computer.
- ARP Cache Poisoning or ARP Spoofing: This MITM attack generally targets businesses and enterprises. A hacker gains access to a company internet network and uses ARP Spoofing to modify their IP and MAC address to make it seem like they are another network device. When a computer on the network sends data to another network device, the data is redirected to the hacker’s fake device instead.
- HTTPS Spoofing: Normally, HTTPS websites are secure and trusted, instead of HTTP. However, that is not always the case because some hackers use HTTPS Spoofing to trick victims into a false sense of security in order to steal their account credentials. In this MITM attack type, a hacker registers a domain that is similar to the legitimate website, for example establishing a typo in the true domain name. The hacker also registers a security certificate (SSL) to ensure it “appears” genuine. A fake email is sent by the hacker, embedding a weblink or URL within the message enticing the victim to click on the link and visit the website. Any action carried out on this fake website is seen by the hacker.
- Wi-Fi Eavesdropping: A hacker connects to the same public Wi-Fi as their victim and intercepts the connection between the public Wi-Fi network and the victim. The hacker steals data transferred between the victim and the website they are connected to, including browsing data and unprotected device files. Hackers may also create their own public Wi-Fi network with a similar name as a true public Wi-Fi network. They will remain in wait near the valid public Wi-Fi establishment. The victim unknowingly connects to the fake public Wi-Fi network, believing it to be genuine. Anything performed while connected to the fake public Wi-Fi network, that is not encrypted, will be tracked by the hacker. This attack may also be accomplished by connecting to the existing public Wi-Fi and “listening in” on the victim’s activity, without ever having to create a fake public Wi-Fi network. This means that even if you are connected to the authentic public Wi-Fi network, your activity may still not be safe!
- SSL Hijacking: Anyone running behind on software and operating system patches are at risk for using breakable encryption. This is due to the plethora of ways in which internet traffic may be encrypted and they change over time (for example, SSL v3, TLS 1.0/1.1/1.2/1.3+). Older protocols for encryption like SSL naturally become unsafe as time goes on. SSL Hijacking occurs when a victim tries to connect to a website, a hacker intercepts the request and creates an independent and legitimate request to that website’s server. Once the server responds to the hacker, they create an unencrypted format of the website and send it to the victim. This way, the attacker poses as the website (or application). When the victim carries out an action on the fake website, the server automatically connects to the authentic website. While it may look like the victim is interacting with the real website, all their data is routed through and captured by the hacker. Most modern devices use TLS (Transport Layer Security) encryption over SSL (Secure Sockets Layer) making this type of hijacking very difficult.
Protect yourself from MITM attacks by being aware of phishing attempts. If you receive an important email from a trusted source, pay attention to the email sender information. Make certain that the email domain is accurate/legitimate. When using public Wi-Fi, always use a Virtual Private Network (VPN) so that your online activities remain encrypted and a hacker will not be able to see your activities or account credentials. Also, be certain you are connecting to the legitimate Wi-Fi network and most importantly, avoid doing any sensitive activities (such as online banking) on a public Wi-Fi network that you cannot trust. Lastly, use security protection software for your device (think anti-virus, anti-malware, anti-spyware tools).


