Password Attacks
Password attacks are one of the most common ways for threat actors to gain access to your data, by stealing your password. No matter how often we are told to create strong passwords, many of us still use the same basic password in multiple places simply because we can remember them! How do password attacks work and how can we reduce the risk of one of them attacking us?
There are several different methods to cracking a user’s password in order to gain unauthorized access to a system and/or data:
- Phishing – attackers will trick users into replying and sharing user credentials
- Dictionary Attacks – password lists easily obtainable on the Internet are used by attackers to use single words in common language dictionaries in order to break into a system, relying on the tendency of people to use a real word as their password.
- Brute-Force Attacks – trial and error methods of working through every combination of letters and numbers, generally successful the shorter the password.
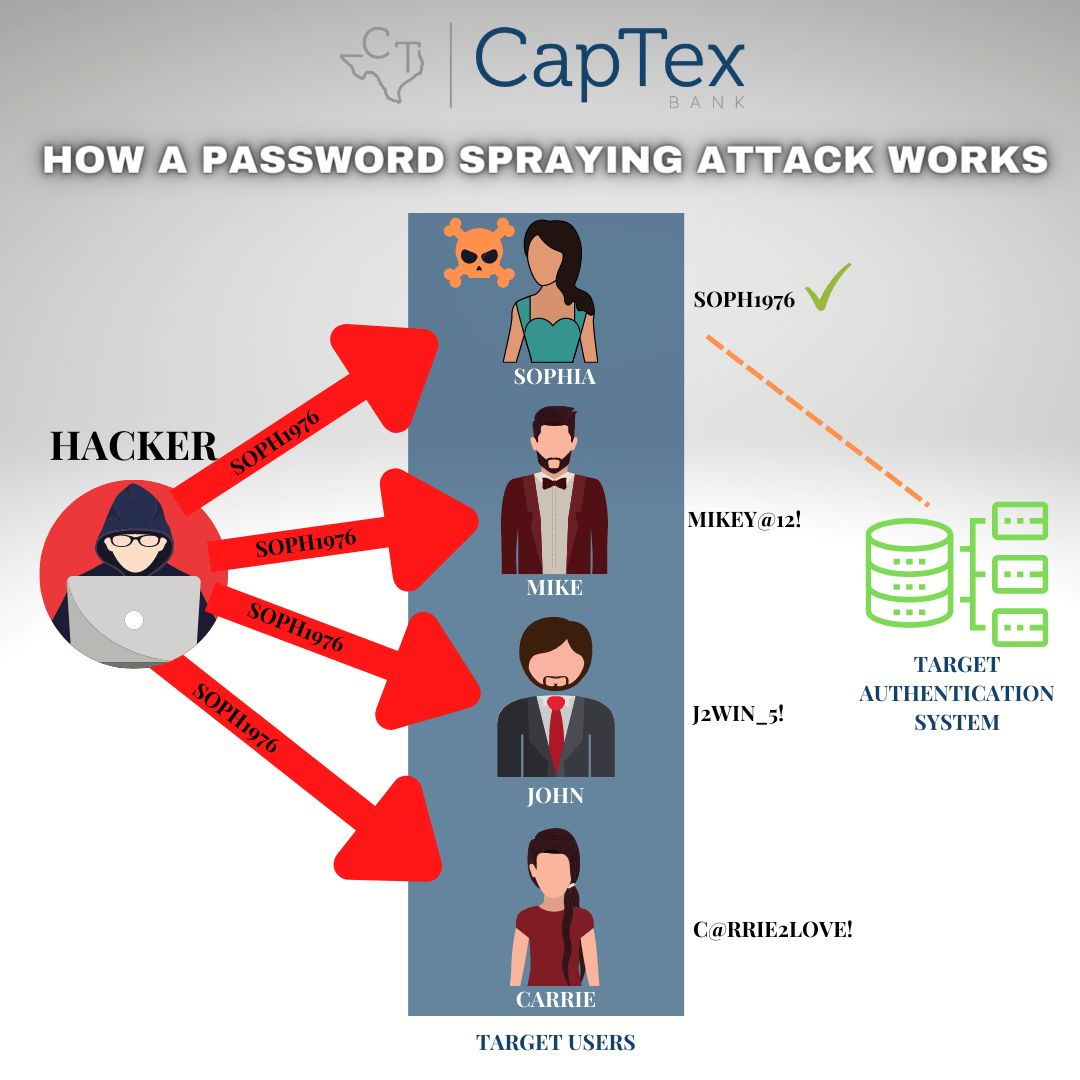
- Password Spraying or Credential Stuffing – uses stolen credentials through social engineering attacks like phishing, taking the password gained and attempting its use across an entire environment or multiple systems and applications.
- Keylogger Attacks – spyware that allows hackers to obtain information secretly by recording a user’s keystrokes when typing anything at all.
- Rainbow Table Attacks – a key to deciphering encrypted passwords stored on a system.
Hackers are quick and highly sophisticated in obtaining passwords because they use automated tools.
There are multiple ways to implement protections for password attacks. Multi-Factor Authentication (MFA) that cannot be bypassed by phishing attacks is one method. Another method is to ensure you have different passwords set for all of your crucial accounts. Lastly, passwords should be long and complex or in the form of a passphrase and should be changed, at a minimum, annually. Reviewing your security and password policies should be done regularly to remain agile and refine security as new technology emerges. With the right protections in place, passwords can remain an important line of defense.


