Ransomware Attack
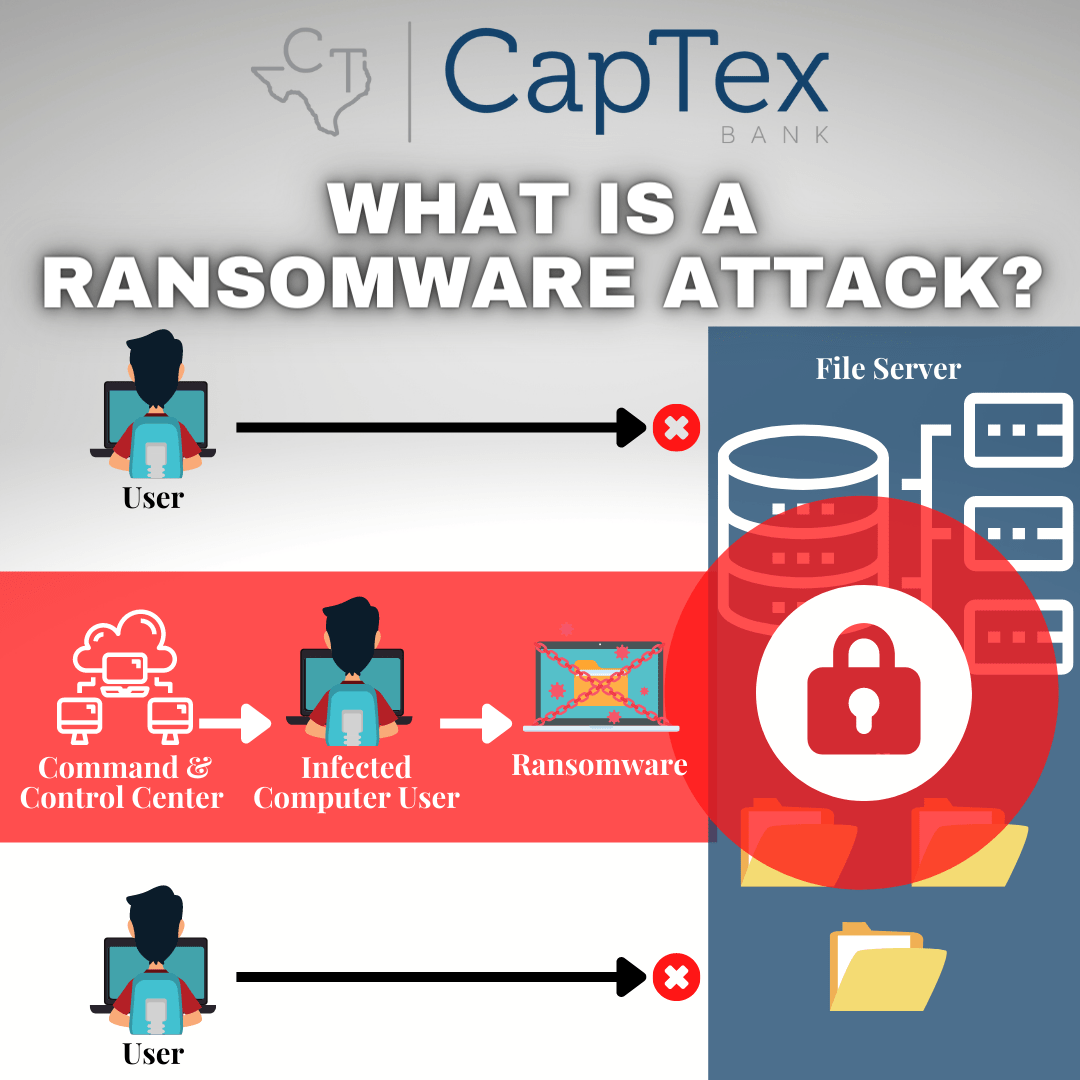
The term “ransomware” appears frequently in today’s world and there is good reason for that since ransomware is responsible for a large portion of all cyberattacks. This malware employs encryption to hold a victim’s information at ransom. The hacker uses it to encrypt a user or organization’s critical data so that they cannot access files, databases, or applications.
They then demand that the victim pay a ransom in order for the bad actor to provide access to the information, normally in the form of a decryption code. This threat has grown exponentially over the past several years and it generates billions of dollars in payments to cybercriminals, inflicting significant damage and expenses for businesses and governmental agencies.
How do you get ransomware on your device? The leading point of infection is falling victim to phishing social engineering attacks, whether it is in the form of a suspicious email, text or voicemail. If you receive an email, call or text asking you to download software or pay a certain amount of money, don’t click on anything or take any direct action from within the message. This will prevent you from downloading malicious content or falling victim to a costly scam.
Protect your device (and yourself) from ransomware
- Use a comprehensive security solution to protect your devices from cyber threats
- Update your devices’ software (including your security software) frequently
- Enable Multi-Factor Authentication (MFA) in order to provide an extra layer of security
- Limit privileged user permissions
- Become security aware at all times – train and educate employees about the various types of threats they may encounter and what they should do
- Always browse safely online, being careful where you click and only download applications from trusted sources
- Only use secure networks and avoid using public Wi-Fi networks
If you fall prey to ransomware, take these steps to assist in getting your data back:
- Act immediately!
- Remove the infected device from your network and consider disconnecting network segments to minimize spread and to contain the impact of the ransomware
- Rely on your system and data backups to restore your infected files
- Change all of your account passwords, creating passwords that are complex
- When creating complex passwords, be sure to diversify them across all accounts
- Never pay the ransom as there is no guarantee that the ransomware developers will even send you a decryption tool once they have received your payment
Stopping ransomware requires prevention, ending the entry point into a system and the most effective ways for stopping these attacks relies on gaining full visibility within your systems, prevent and block known threats and detect and analyze unknown threats in files and URLs. Ransomware is a raging battle and cyber attackers are employing increasingly sophisticated means to infect devices and hijack data by encrypting it. Your systems and data that power all aspects of your business operations are completely at risk if your devices are not secured.


