SQL Injection Threat
SQL is a programming language that allows programmers to communicate to large databases using essentially transparent text. It can access and exploit data held in a number of tables on a server.
When it comes to websites, those tables might include sensitive items like usernames, passwords, credit card numbers, etc. The problem with this is that websites can occasionally be tricked into running malicious SQL queries when proper precautions are not in place.
This type of cyber attack is called a SQL Injection. Most extensive websites or web applications will usually have at least one interactive area in which content changes based on input. Examples are: search queries, username and password entries, and data submission.
When these inputs are received by the web server, they are translated into simple SQL queries in order to respond with the correct information. Or the web server may check input against data from a table or add data to a table for storage (like a new user review for a product or service).
If a website is not properly protected, hackers can make modifications to their inputs to form malicious queries that create disastrous ramifications.
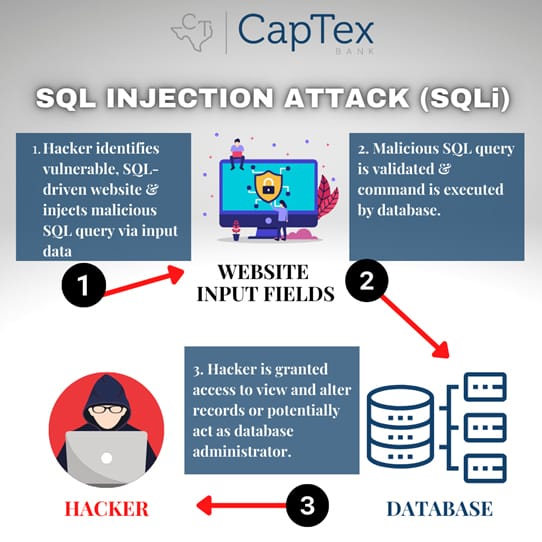
SQL Injections can lead to an attacker accomplishing the following:
- Locating administrator credentials
- Elevating privileges
- Compromising back-end infrastructure
- Spoofing
- Tampering
- Repudiation
- Disclosing sensitive information
- Denial-of-Service (DoS) attacks
These attacks can range in complexity depending on the attacker’s skills. There are various types of SQL Injections:
- In-Band SQL Injection: This is a common form of SQLi attack in which a hacker can see the results of their queries on the same screen as their input and can use the data that appears to gather information they need about the database in order to construct a query to display, delete, or manipulate certain data.
- Blind SQL Injection: Hackers can not necessarily see the results of queries in this particular attack type – but they can slowly piece together information based on failed pages, response times, and other subtle pieces of data that appear over the course of several queries. This is a much more sophisticated attack. A systems vulnerabilities and database software versions can be learned based upon this type of an attack. Knowing this information can allow hackers to create harmful queries.
- Out-of-Band SQL Injection: If a Blind SQL Injection query is too hard to piece together, attackers can sometimes force the database to send a DNS request to their own site. If this request arrives in tact on the hacker’s site where they can monitor requests and other activity, then it provides them with more information about potential vulnerabilities that they can use to advance their attack.
Identifying a SQL Injection begins with identifying application and system vulnerabilities. This can be accomplished by running SQL Injection attack scanning tools – once identified the malicious injections can be removed and patches may be applied. In addition, all passwords will need to be updated. All in all, remediation is possible.
These types of attacks can be prevented by using modern and trusted technologies and content management systems. Running frequent updates on website platforms in order to patch vulnerabilities will add protections, as well as using only add-ons or plugins from the most trusted sources. Restricting inputs, such as requiring specific characters within a username, before submitting a query will add another speedbump to a hacker’s progress. Databases should not store things like user passwords as plain text – they should be hashed or encrypted using tough algorithms. Same applies to credit card numbers and other sensitive data. Lastly, hackers can retrieve information from the errors that result from a failed query; therefore, the most simplistic of error messages should be reflected so that hackers do not receive information that may allow them to spot a weakness.
Many factors must be considered when it comes to SQL Injection attacks and it can become overwhelming if they occur. All in all, remediation is possible with the proper security monitoring tools.


